How To Use Netstat To Detect Spyware
 Source: Windows Cardinal
Source: Windows Cardinal
On Windows 10, netstat (network statistics) has been around for a long time, and it'southward a command-line tool that y'all tin use in Command Prompt to brandish statistics for all network connections. Information technology allows you to understand open up and connected ports to monitor and troubleshoot networking problems for arrangement or applications.
When using this tool, you tin can list active networks (incoming and outgoing) connections and listening ports. You tin can view network adapter statistics likewise as statistics for protocols (such equally IPv4 and IPv6). You can even display the current routing table, and much more than.
In this Windows 10 guide, we'll walk you through the steps to use the netstat command to examine connections to find open up and connected network ports.
- How to use netstat on Windows x
- How to utilise netstat parameters on Windows ten
- How to search netstat details on Windows x
How to use netstat on Windows 10
To get started with netstat, use these steps:
- Open Kickoff.
- Search for Command Prompt, right-click the elevation issue, and select the Run as administrator option.
-
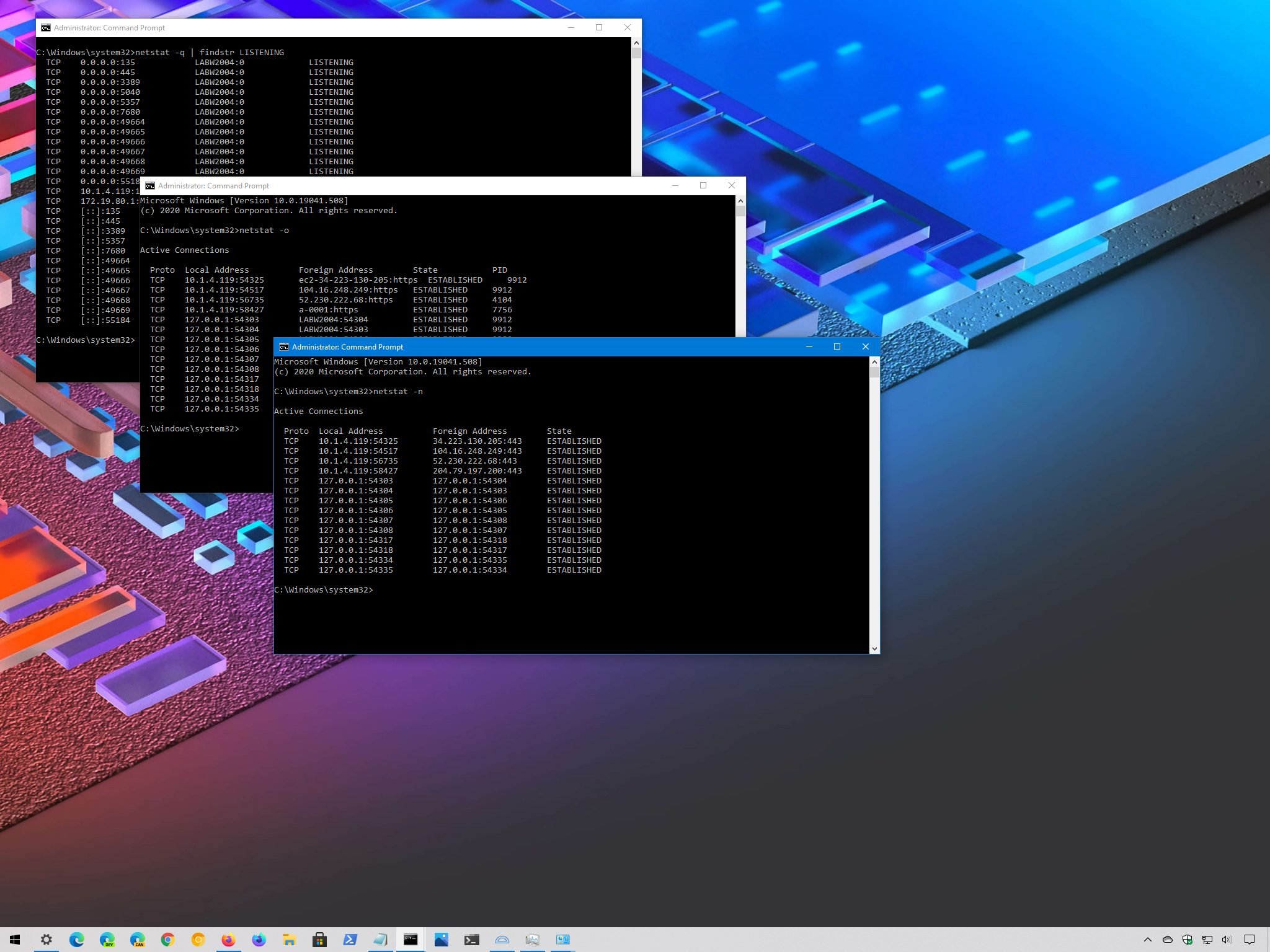
Type the following command to show all active TCP connections and printing Enter:
netstat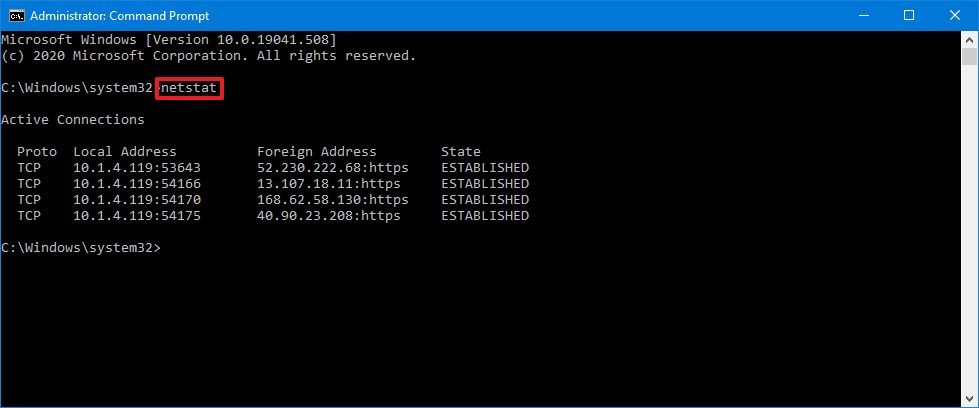 Source: Windows Central
Source: Windows Central -
(Optional) Type the following command to display agile connections showing numeric IP address and port number instead of trying to decide the names and press Enter:
netstat -n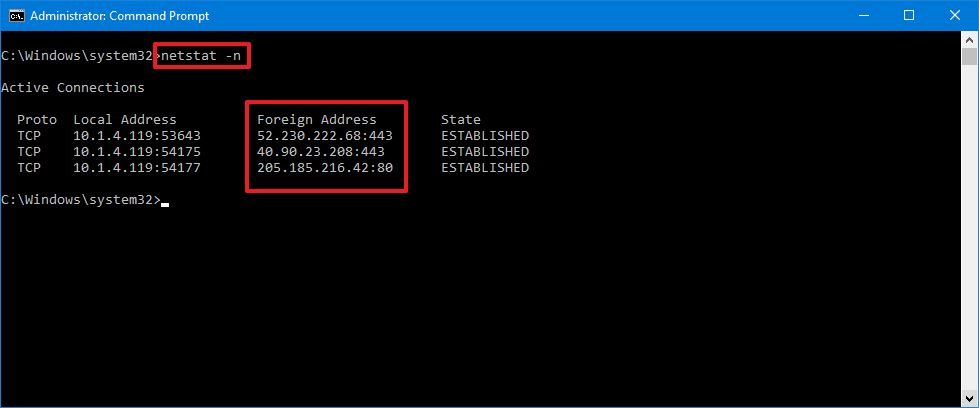 Source: Windows Central
Source: Windows Central -
(Optional) Blazon the post-obit command to refresh the data at a specific interval and press Enter:
netstat -n INTERVALIn the command, make sure to replace INTERVAL for the number (in seconds) yous want to redisplay the information.
This example refreshes the command in question every 5 seconds:
netstat -northward 5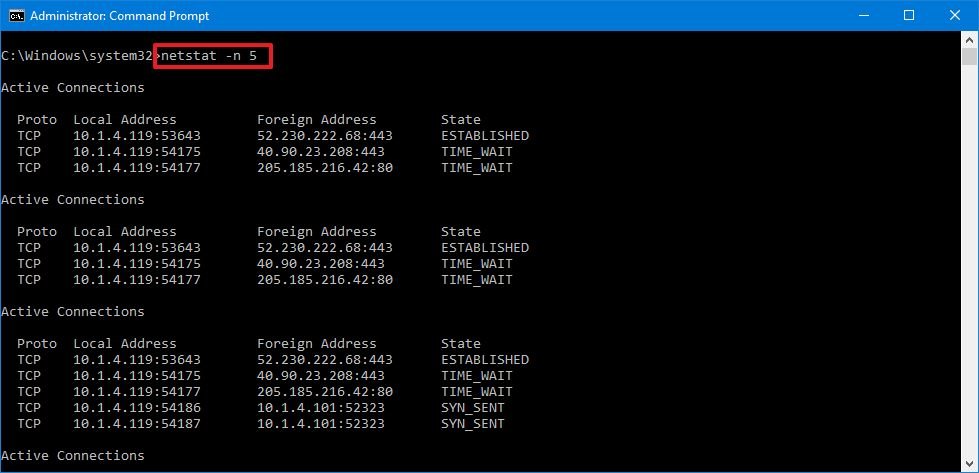 Source: Windows Primal
Source: Windows Primal Quick note: When using the interval parameter, you tin can stop the command using the Ctrl + C keyboard shortcut in the console.
Once you execute the control, it'll return a list of all active connections in four columns, including:
- Proto: Shows the connectedness protocol (TCP or UDP).
- Local Accost: Shows the computer'south IP address followed by a semicolon with a port number of the connection. The double-semicolon inside brackets indicates the local IPv6 address, and "0.0.0.0" refers to the local address too.
- Strange Address: Lists the remote device'due south IP (or FQDN) address with the port number after semicolon port name (for instance, https, http, microsoft-ds, wsd).
- State: Indicates where the connectedness is active (established), the local port has been closed (time_wait), and the plan hasn't closed the port (close_wait). Other condition include, closed, fin_wait_1, fin_wait_2, last_ack, listen, syn_received, syn_send, and timed_wait.
How to use netstat parameters on Windows 10
The tool too includes several parameters that you can apply in Command Prompt to display different data about the network connections.
Evidence agile and inactive connections
The netstat -a control displays all agile and inactive connections, and the TCP and UDP ports the device is currently listening.
 Source: Windows Cardinal
Source: Windows Cardinal
Show executable information
The netstat -b command lists all the executables (applications) associated with each connectedness. Sometimes, applications may open up multiple connections.
 Source: Windows Central
Source: Windows Central
Testify network adapter statistics
The netstat -e command generates a statistic of the network interface, which shows data like the number of bytes, unicast and not-unicast sent and received packets. You tin also meet discarded packets and errors and unknown protocols, which can you troubleshoot networking problems.
 Source: Windows Cardinal
Source: Windows Cardinal
Show FQDNS for foreign addresses
The netstat -f command shows the fully qualified domain proper name (FQDN) for foreign addresses. For example, "server-54-230-157-50.otp50.r.cloudfront.net:http" instead of "server-54-230-157-50:http" or "54.230.157.50".
 Source: Windows Central
Source: Windows Central
Evidence numerical form
The netstat -northward command displays the addresses and ports in numerical form. For example, 54.230.157.l:443.
 Source: Windows Central
Source: Windows Central
Bear witness process ID
The netstat -o command shows all agile TCP connections similar netstat, simply with the difference that adds a fifth column to brandish the Process ID (PID) for each connection. The processes available in this view are the aforementioned in the "Details" tab of Chore Manager, which also reveals the application using the connectedness.
 Source: Windows Central
Source: Windows Central
Show connections by Protocol
The netstat -p can be used to display connections per-protocol that you accept to specify using tcp, udp, tcpv6, or udpv6 next to the control. For example, you tin can utilize the netstat -p tcp to view a list of TCP connections.
 Source: Windows Fundamental
Source: Windows Fundamental
Show listening and non-listening ports
The netstat -q commands can produce a list of all the connections with the listening and leap non-listening ports.
 Source: Windows Key
Source: Windows Key
Show statistics past Protocol
The netstat -due south shows network statistics for all available protocols, including TCP, UDP, ICMP, and IP protocols (version four and 6).
 Source: Windows Central
Source: Windows Central
Show routing tabular array
The netstat -r command displays the electric current network routing tabular array that lists all the routes to destinations and matrics known by the device, for IP version four and version half dozen (if applicable). If the returned information looks familiar, it'due south because you can likewise output the data using the route print command.
 Source: Windows Central
Source: Windows Central
Show offload state connections
The netstat -t control generates a list of the current connection offload country. The offload state refers to the TCP Chimney Offload, which is a characteristic that transfers the network workload from the processor to the network adapter during data transmissions. The "InHost" value indicates that offloading isn't enabled, and the "Offload" means that the feature is transferring the workload to the network adapter. (This feature is only present on supported network adapters.)
Evidence NetworkDirect connections
The netstat -x is some other supported command on Windows 10, and it produces a list of NetworkDirect connections, shared endpoints, and listeners.
NetworkDirect is a specification for Remote Direct Retention Access (RDMA), which is a process that allows fast data transfers using the network adapter, freeing up the processor to perform other tasks. Usually, you'll never use this command unless y'all're using the server version of Windows or a high-operation awarding with a network adapter that supports this feature.
Show connectedness template
The netstat -y control displays TCP connections templates for all connections.
 Source: Windows Central
Source: Windows Central
Combine parameters
When using the netstat command, yous can also combine the parameters to display various information together for many cases.
For example, the -east parameter can also be used with the -due south parameter to run across statistics for each bachelor protocol, and the -o parameter tin be combined with -a, -north, and -p as necessary.
 Source: Windows Primal
Source: Windows Primal
With the netstat -p control, y'all append the s parameter, yous can brandish statistics from fifty-fifty more protocols, including icmp, ip, icmpv6, and ipv6.
Also, when using more than one parameter, you can combine them with a single -. For case, instead of writing the command netstat -due east -s, you can write it like this: netstat -es.
 Source: Windows Central
Source: Windows Central
If you want to see all the available parameters and boosted help, you tin always employ the netstat /? command.
How to search netstat details on Windows 10
In addition to displaying all the available statistic information, you can too output only the sure details y'all need using these steps:
- Open Showtime.
- Search for Control Prompt, right-click the top result, and select the Run every bit administrator option.
-
Type the following command to list all the connections that have the state set to LISTENING and press Enter:
netstat -q | findstr CordIn the command, make sure to supercede STRING for the information you want to list. Also, the findstr option is case sensitive, which means that you must enter the string yous want to find with the exact casing.
This example lists all the connections that have the state set up to "LISTENING."
netstat -q | findstr LISTENING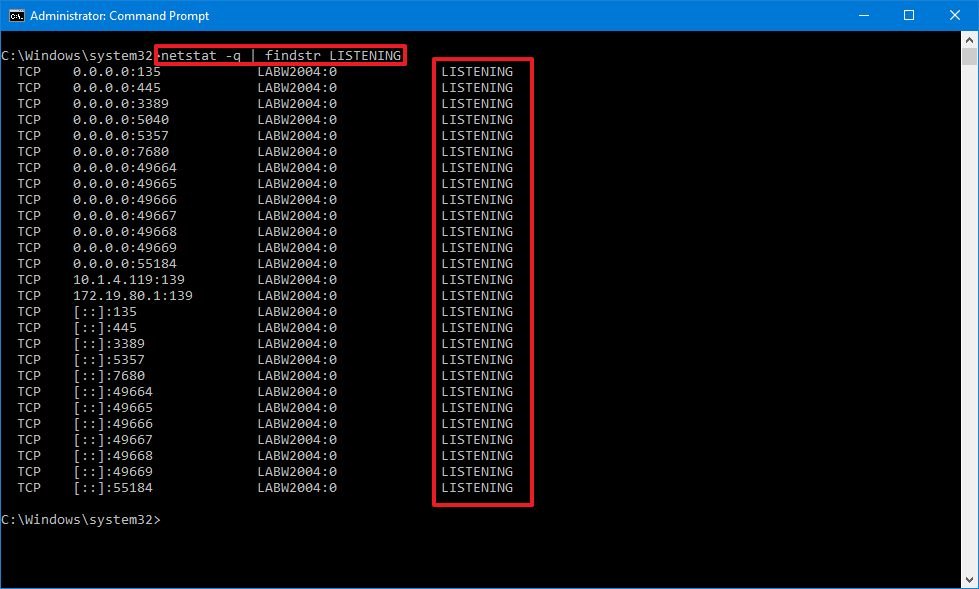 Source: Windows Central
Source: Windows Central This other example shows all the connections from a foreign server FQDN, in this example, Amazon:
netstat -f | findstr amazonAs yous tin run into, you but need to type role of the string to return a result.
The findstr control isn't part of the netstat tool. Information technology'due south a simple command to search for a text cord in a file, just you can use information technology with many of the netstat commands to make more sense of the information yous're viewing.
The netstat command is available on Windows x, only you lot can also notice information technology on Windows Server, Windows 8.x, Windows 7, and older versions. The tool is non exclusive to Windows either, every bit information technology'south besides bachelor across platforms, including Linux and macOS. Even though the parameters and syntax may be different, they all are very like.
More Windows 10 resource
For more than helpful articles, coverage, and answers to mutual questions about Windows 10, visit the following resources:
- Windows 10 on Windows Cardinal – All yous need to know
- Windows 10 help, tips, and tricks
- Windows 10 forums on Windows Key
We may earn a commission for purchases using our links. Learn more than.

Then good
Review: Lenovo'southward Yoga 9i Gen 7 with OLED and speaker bar is simply superb
The Lenovo Yoga 9i fourteen Gen7 for 2022 brings an all-new smoother, more modern design while amping up the brandish and audio to new highs. But while the Intel twelfth Gen P-series processor blows abroad fifty-fifty Apple's M1 for performance, bombardment life is this laptop'due south ane weak spot. Hither's our total review.
How To Use Netstat To Detect Spyware,
Source: https://www.windowscentral.com/how-use-netstat-command-windows-10
Posted by: reamhiscaralls.blogspot.com






0 Response to "How To Use Netstat To Detect Spyware"
Post a Comment